How To Break Into Any Password Protected Windows/Mac Computers
By Shaon, Gaea News NetworkMonday, November 8, 2010
Do you really think that all your important files and documents are safe behind the haven of the password protected log on screen? Well think again. Because its as simple as dragging and dropping your files onto a pen drive. Well tell you how.
For Windows
To break into your windows filesystem which is not encrypted (I you are not sure if you have encryption, You probably don’t). all you need is a proper live linux distribution like Ubuntu or anything else for that matter. To get a live cd all you need to do is to download the ISO and burn it. Make sure that your BIOS is set to load your DVD/CD Rom first. Then Select the option Try it from the main menu. Well you have now booted into your very own OS with no holds barred accesses to any NTFS based Windows Filesystem.
Now there just might be a hitch in this proscess where you wont be able to copy some files as you don’t have access to the root. To solve this issue you have to go to Applications > Accessories > and select the Terminal. Type in ‘gksudo nautilus’ while leaving the password blank when prompted. Voila you now have each and every file at your beck and call.
So how to save yourself from being subjected to an exploit like this? Well all you need to do is to encrypt your files and ideally your OS as well.
Say you might be thinking that you would break into someone’s Windows Operating system in its full glory. You really need not look further than the Sneaky Command-Line Fu, a Linux based System rescue disk. You really have to be careful with this one and follow the instructions to a t. download the iso file from here https://www.sysresccd.org/Download and burn as the previous method. If everything goes fine you will be presented with a CUI type in fdisk -l. You will be presented with all the hard drive partitions you have. The drives would be named in the format /dev/sda3.
Make sure that you note the number of the partition right. Then run the following commands
ntfs-3g /dev/sda3 /mnt/windows o force
cd /mnt/windows/Windows/System32/config
All that is left is to edit the SAM file in the folder.
chntpw l SAM
chntpw u “Shaon Banerjee” SAM
Make sure that You replace “Shaon Banerjee” With the name of the account you have to hack.
Then in the next screen that would follow you are required to select the first option. Voila you have just erased the User’s Password. Make sure that you select Y when prompted whether you would want to write hive files. When you boot into the windows next time you would be able to log in just like that without the requirement of the Password.
But the Achillies heel of this method lies in the fact that the hack wont be able to aces encrypted filesystems.
An even then you could go the old fashioned way and Brute Force your way in to the system. You can use Ophcrack Live CD and boot it up. It will start to attempt on passwords after an understandably long load time. Know what it will also give you an unrestricted access to the encrypted files.
But then again if the user has a 14 letter alpha numerical password you are pretty much on your own.
The mac users who must have been enjoying the article so far don’t have much to rejoice either. We are now delving deep into Apple land and try and crack some Macintosh passwords. I will say only this that to hack into a mac you won’t even need to download stuff.
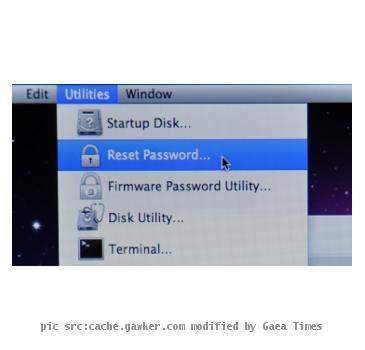
When you can use third party tools to hack into a mac but what you actually need to get into a password protected Snow Leopard would be to simply the Mac OS X installer CD. hold the C key as you boot up and you would be directed to the Mac OS X installer. There if you look closely under the Utilities tab you would see that an option exists titled “Reset Password” Well so much for Subtlety. Follow the Windows that pops up and choose the drive where the OS is installed. Select the user account to reset and let Apple’s legendary “Usability” take care of the rest. You would need to provide a new password and you would be good to go. You won’t be able to unlock the Keychain, so if you’re trying to get into something that has another layer of password protection, you won’t be able to access it.
But what if you don’t have a Live CD around. Well you gotta do the resetting the old fashioned way. Boot up the Mac and hold the Command+S as you hear the jingle. The Mac will load you onto a single user mode and give you the coveted access to the command line. Just enter the following commands
/sbin/fsck -fy
/sbin/mount -uw /
launchctl load /System/Library/LaunchDaemons/com.apple.DirectoryServices.plist
dscl . -passwd /Users/shaonbanerjee Your Password
Be sure to access and run the ls /Users at the terminal. The method is handicapped with the same issue above wherein you wont be able to access anything if there is another password layer protecting the OS.
The only option that would take care of such unwarranted intrusions in a Mac is to use a two pronged approach. You have to use an encryption utility like FileVault and TrueCrypt. They understandably prevent any breach even upto the Password resetting screen of the first method. But TrueCrypt will not encrypt the entire drive containing the OS. Also a Firmware password if set up will not allow the machine to boot up even by swapping hard drive or single user mode. Thus ensuring your precious Mac never falls to prey to hackers. The firmware password in its very essence is hackable (Everything is) but that would the crook to fiddle with the Hardware quite a bit. If some one gets that much access to your machine its better to tell him the Firmware Password I guess.
Jokes aside how secure is your PC/Mac. Can we get into your system using these methods? Let us know
Tags: Apple, Linux, Mac, Microsoft, Snow leopard, Windows


Mobil Keluarga Ideal Terbaik Indonesia